Just-Your-Basic-Port-Scanner
Just your basic port scanner - with multiprocessing capabilities & further nmap enumeration.
Use at your own discretion, this program does not support or promote unethical or illegal behavior in anyway. This is simply a free tool to help users with CTFs or other legal endeavors.
Dependencies
- for further enumeration nmap will need to be installed onto your machine
For Linux Users
sudo apt install nmap
Installation
-
Clone this repository.
-
Run the following commands to install dependencies and user permission.
pip3 install -r requirements.txt
chmod +x jybps.py
- Run the binary in the repository
If you want to run it from any directory simply add a symbolic link:
sudo ln -s $(pwd)/jybps.py /usr/local/bin/jybps
Usage & Examples
Basic Syntax:
Interactive Mode Off: (simply add hostname argument)
jybps --hostname {host_name or ip_address} --workers {num} --startport {num} --endport {num}
Interactive Mode On: (simply remove hostname argument) remove hostname argument 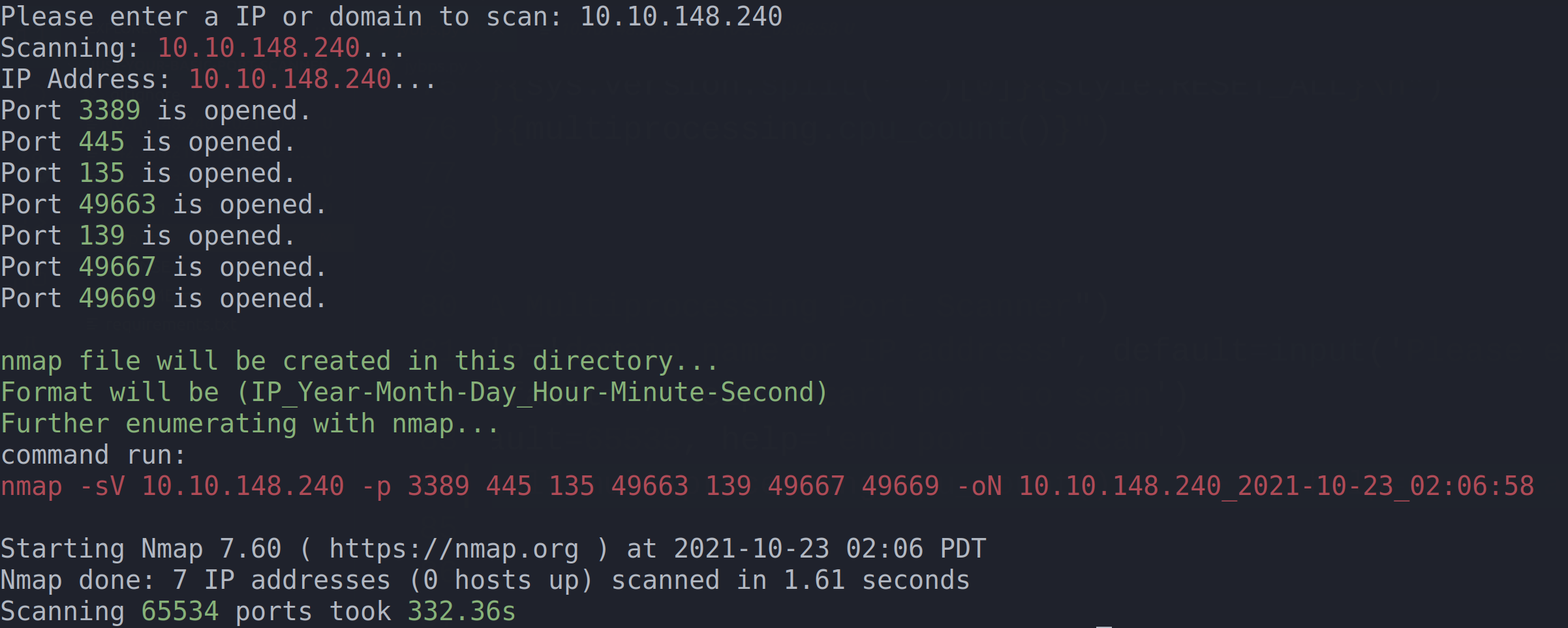
Default starting port is 1 and ending port is 65535 if no arguments are passed
If no hostname is passed then interactive mode will be on and the user must provide a FQDN or IP to scan ports 1-65535
Workers dictate the granularity of the port checking subprocesses. Workers default to CPU count * 2 + 1 (recommended to use 100-200)
Example use to scan all ports (needs a symbolic link to run in any directory)
jybps --workers 200
To scan ports 1:1024 without turning on interactive mode
jybps --hostname www.fakedomainname.com --workers 200 --startport 1 --endport 1024
To scan ports 1:1024 turning on interactive mode
jybps --workers 200 --startport 1 --endport 1024
Help
jybps -h